Blog
Sharing the latest news from emerging cyber threats to CMMC, best practices and cybersecurity insights, our blog features resources for executives and business leaders from our cybersecurity expert CISOs.

How Volt Typhoon Works and 4 Indicators You’ve Been Compromised

5 Things to Know About Volt Typhoon: The Stealthy Chinese Cyber Threat Targeting U.S. Critical Infrastructure

SIM Swap and SIM Swap Fraud. What is it? How does it work? How can it be prevented?

Trusted Internet, LLC Announces $500,000 Cyber Security Warranty and Cyber Insurance Options for its MSSP and MDR Services

Trusted Internet Adds Senior Healthcare Executive Adam John as Virtual Chief Information Security Officer

Trusted Internet Guidance: Apple’s threat notification on “mercenary spyware”

Trusted Internet Guidance on the US Cybersecurity and Infrastructure Security Agency Emergency Directive on Microsoft Email Compromise
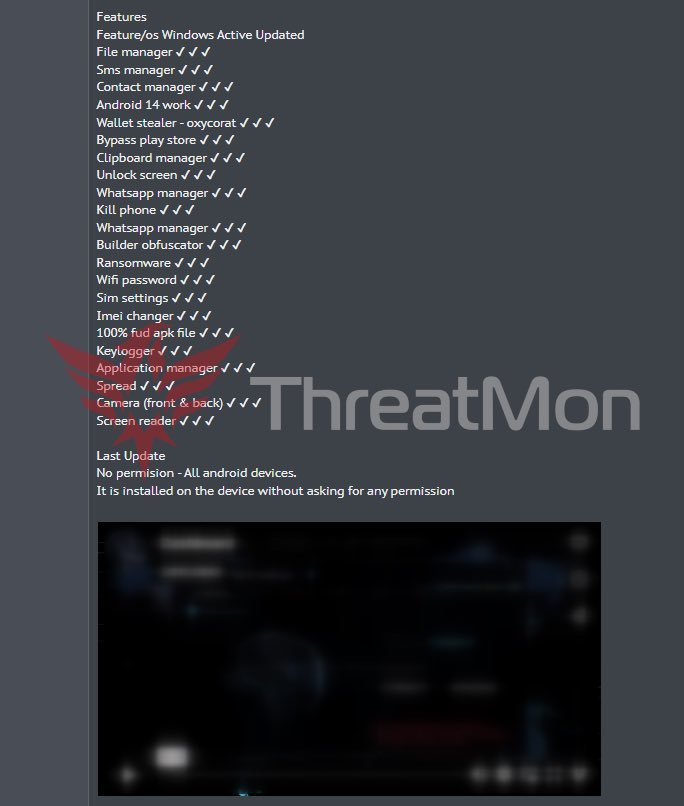
Android Remote Access Trojan (RAT) with Ransomware Implications and Stealing Wi-Fi Passwords
Trusted Internet reporting on ThreatMon’s discovery of the Oxycorat Remote Access Trojan targeting Android.

What happens when you click that link? A Simple Case Study of a Local New Hampshire Small Business.

From the Digital Shadows –the true story of a home WIFI invasion

Are Your Home Security Systems Spying On You?
Lessons learned when selecting an XDR.

Lessons learned from our search for, and integration of, our XDR
Lessons learned when selecting an XDR.

How to create a system security plan, and some of our lessons learned.
Cybersecurity compliance system that meets requirements and makes your life easier.

